11 өөрчлөгдсөн 199 нэмэгдсэн , 2 устгасан
+ 15
- 0
docs/reference/elasticsearch-plugins/authentication-plugins.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
BIN
docs/reference/elasticsearch-plugins/images/ms-graph-authz/01-create-enterprise-application.png

BIN
docs/reference/elasticsearch-plugins/images/ms-graph-authz/02-find-app-registration.png

BIN
docs/reference/elasticsearch-plugins/images/ms-graph-authz/03-get-application-id.png

BIN
docs/reference/elasticsearch-plugins/images/ms-graph-authz/04-create-client-secret.png

BIN
docs/reference/elasticsearch-plugins/images/ms-graph-authz/05-configure-api-permissions.png
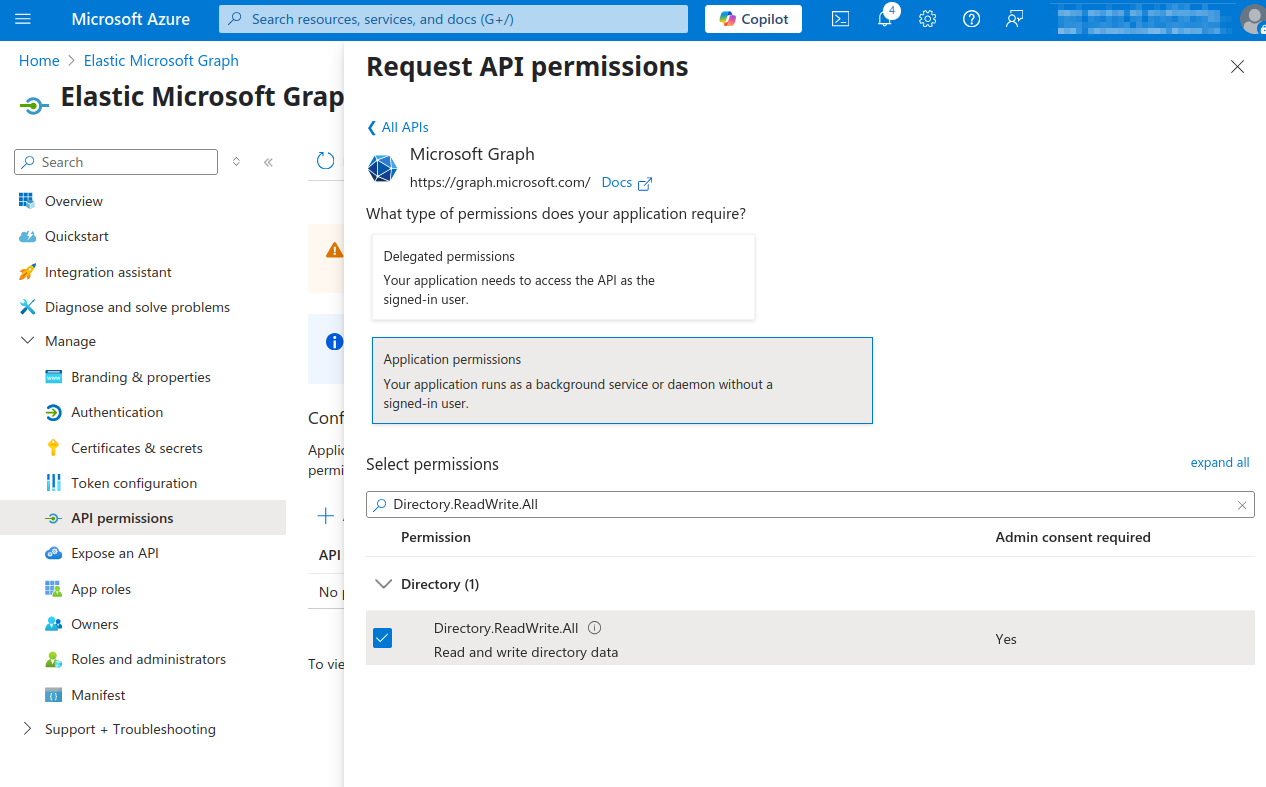
+ 60
- 0
docs/reference/elasticsearch-plugins/ms-graph-authz-configure-azure.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 68
- 0
docs/reference/elasticsearch-plugins/ms-graph-authz-configure-elasticsearch.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 48
- 0
docs/reference/elasticsearch-plugins/ms-graph-authz.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 1
- 1
docs/reference/elasticsearch-plugins/plugin-management.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 7
- 1
docs/reference/elasticsearch-plugins/toc.yml
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||